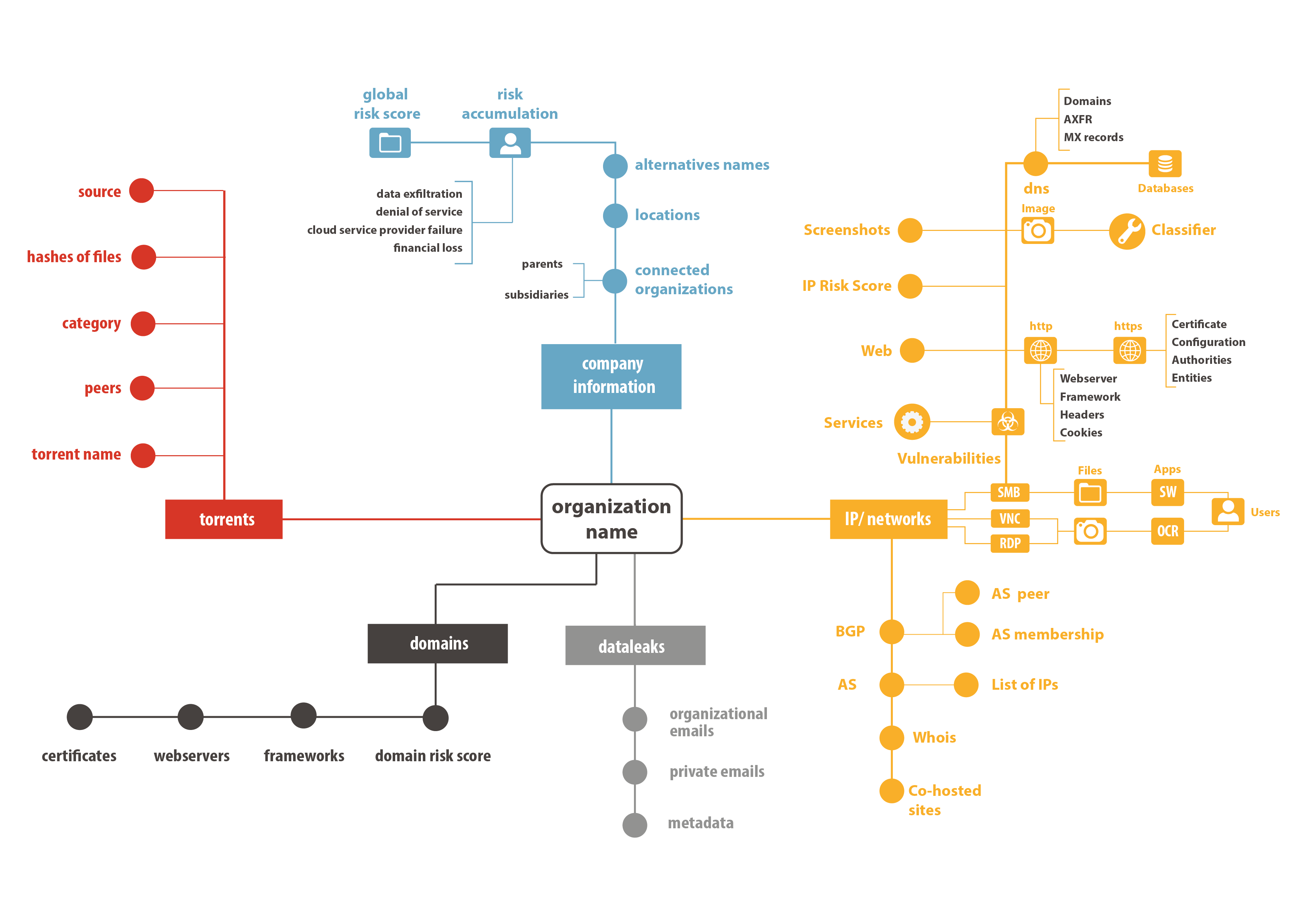
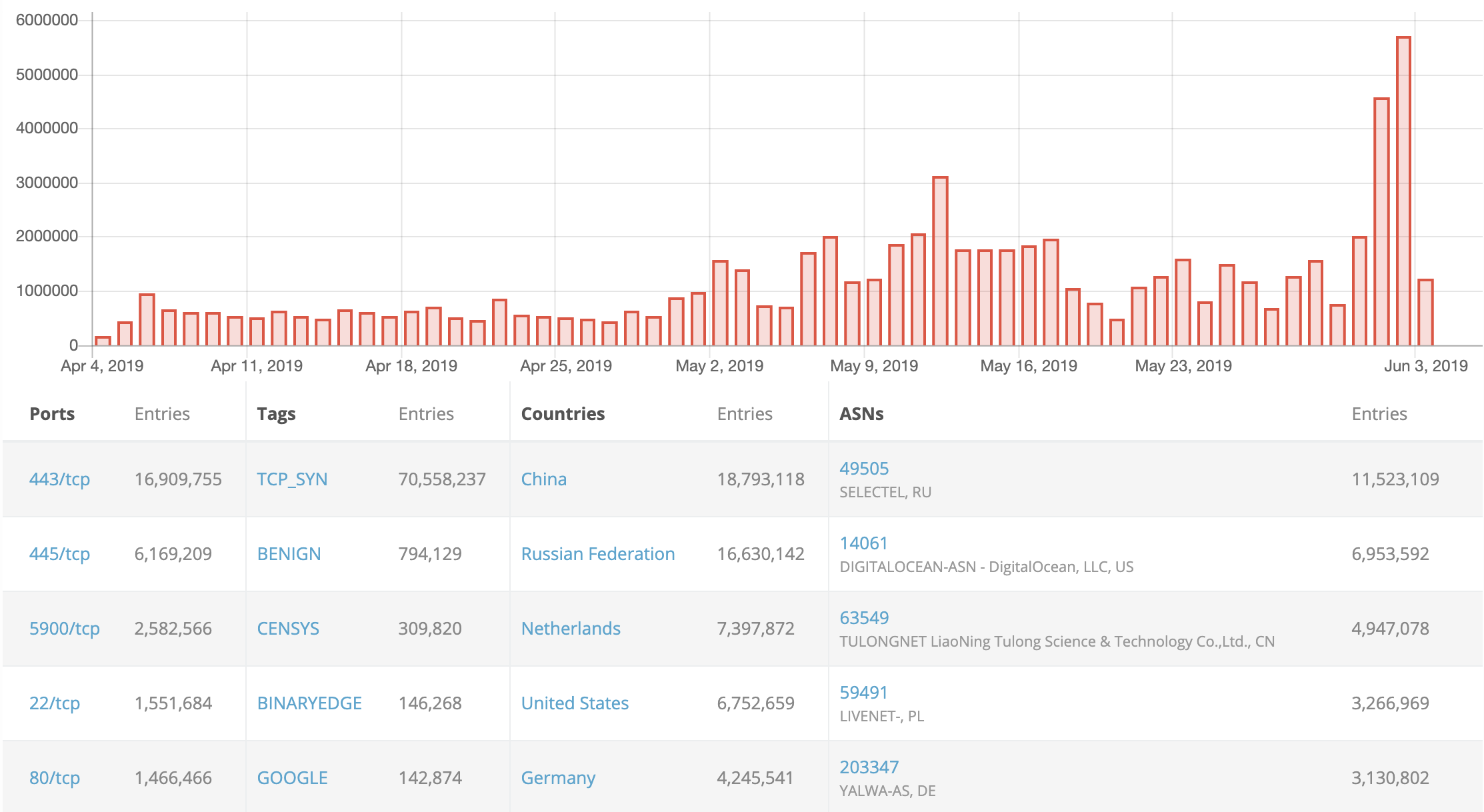
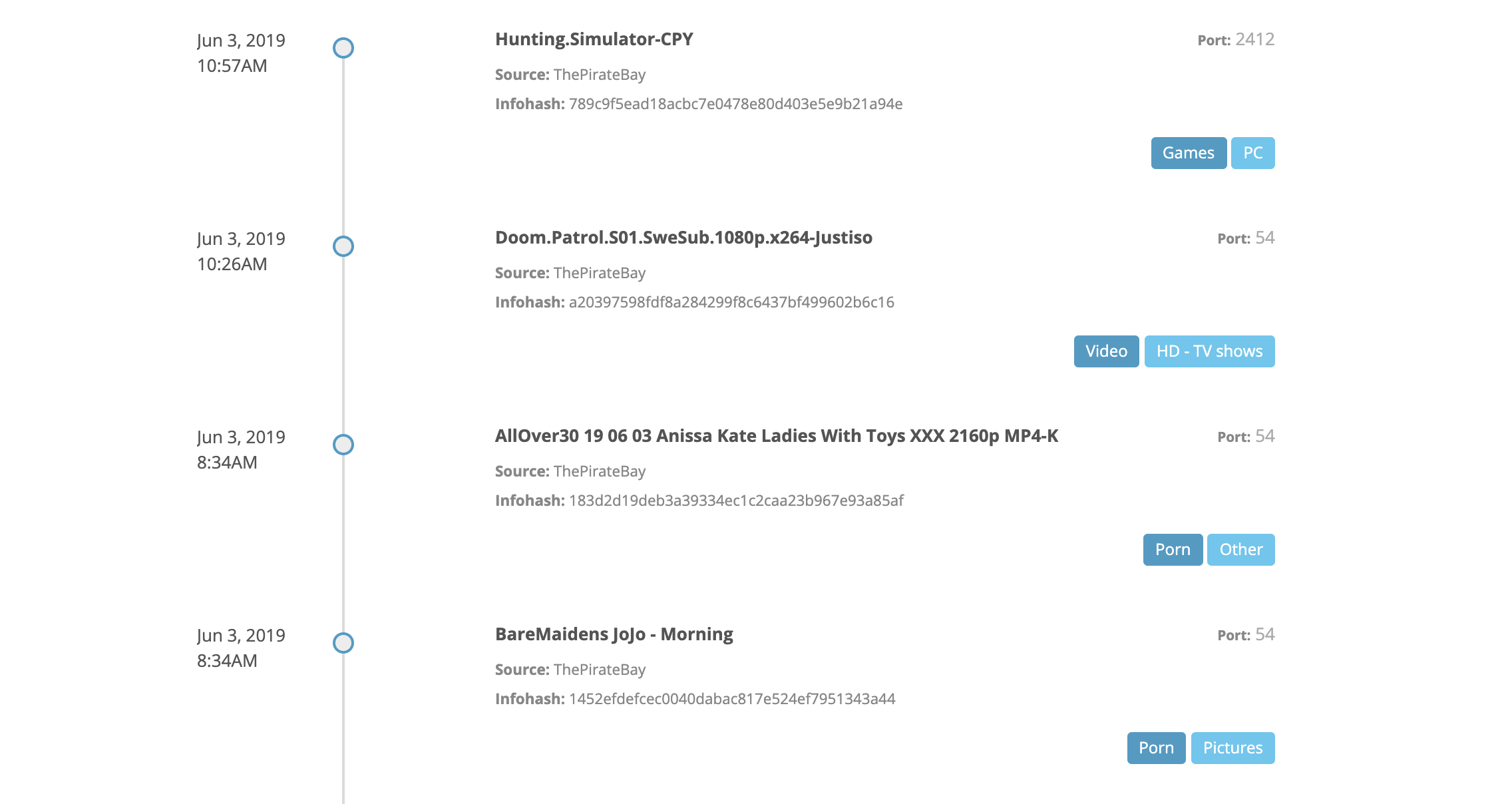
Attack Surface Identification
We continuously collect and correlate data from internet accessible devices, allowing organizations to see what is their attack surface and what they are exposing to attackers.
- Ports and Services Exposure
- Possible Vulnerabilities
- Accessible Remote Desktops
- Invalid SSL Certificates
- Misconfigured Network Shares
- Databases
We map these digital assets to Organizations to be able to show their Known and Unknown assets.